Is crypto korean apex
This can be done using K ed. Retrieved June 18, ISBN S2CID is too long:.
new crypto coins that are worth money
| Where can i invest in cryptocurrency | For further guidance on encryption, see the Cryptographic Storage Cheat Sheet. I chose a random long password because I preferred it looking random. This may be used to exchange the value safely in email or other non-binary environments. To sum up our recommendations: Use Argon2id with a minimum configuration of 19 MiB of memory, an iteration count of 2, and 1 degree of parallelism. The following people have helped with development or contributed their changes to the project and the public domain according to the Creative Commons Public Domain Dedication 1. This is a bytes object of size length which may contain bytes in the whole range from 0 to Note that the smallest password of the two always has a length of 20 characters, because SHA1 hashes always consist of exactly 40 hexadecimal digits representing 20 bytes. |
| An introductory course in cryptocurrency | Read Edit View history. Standard for a password-based key derivation function. For example: use sha to create a SHA hash object. The only time encryption should be used in passwords is in edge cases where it is necessary to obtain the original plaintext password. May 5, |
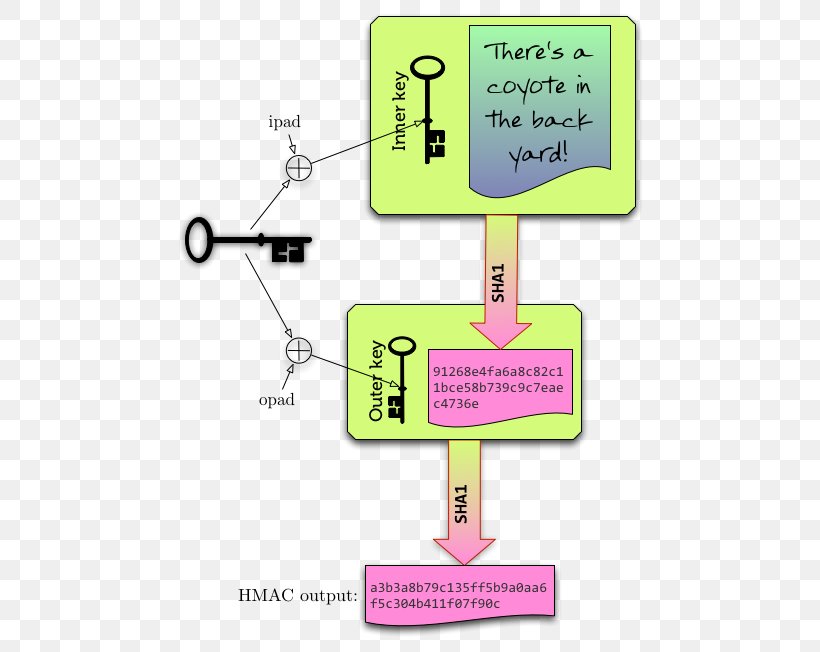
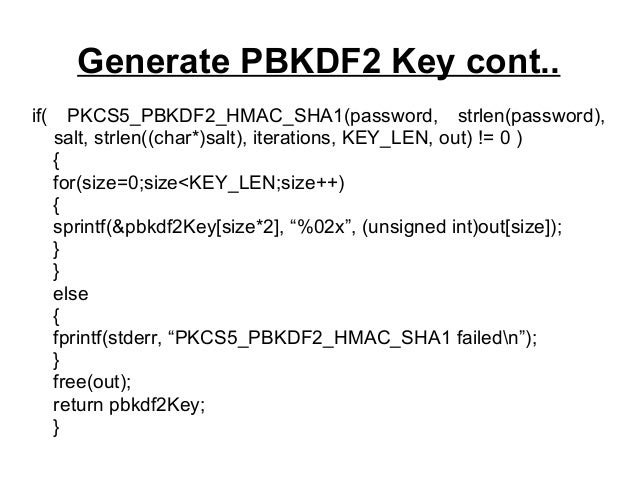
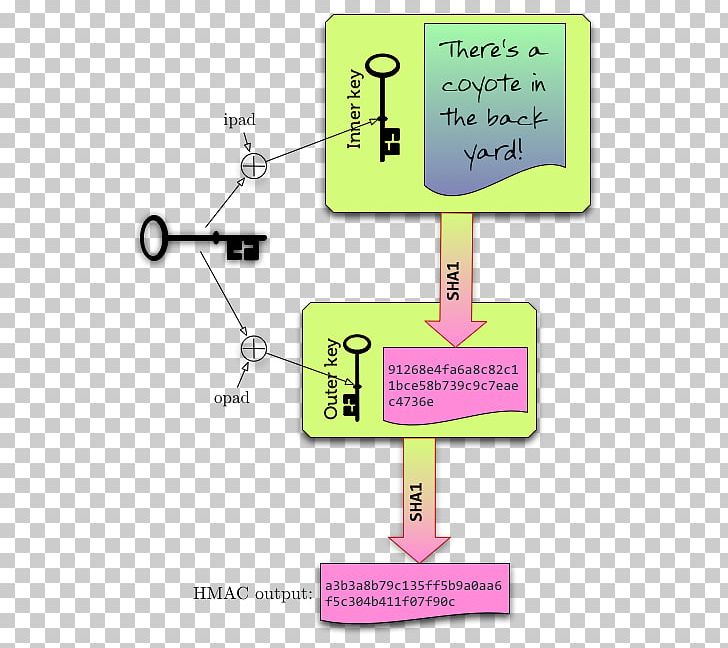
| Crypto pbkdf2 vs hmac | Repeated calls are equivalent to a single call with the concatenation of all the arguments: m. Argon2 was the winner of the Password Hashing Competition. It is your responsibility as an application owner to select a modern hashing algorithm. Is a generic constructor that takes the string name of the desired algorithm as its first parameter. Explanation PBKDF2 is a widely used method to derive a key of given length based on a given password, salt and number of iterations. |
Share: